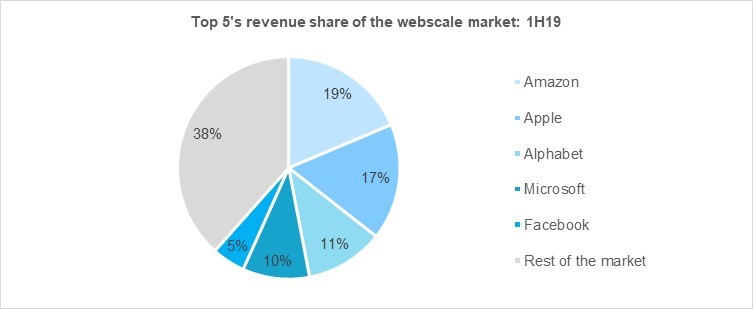
In the beginning, the people of Earth told their truths, voiced their opinions, and advertised their wares and services in print media such as newspapers and magazines.
And the people of Earth looked upon their works, and called it good.
In time, humanity harnessed the power of parts of the electromagnetic spectrum. And lo, the people of Earth told their truths, voiced their opinions, and advertised their wares and services on radio.
And the people of Earth looked upon their works, and called it good.
In time, humanity harnessed the power of more of the electromagnetic spectrum. And lo, the people of Earth told their truths, voiced their opinions, and advertised their wares and services on television.
And the people of Earth looked upon their works, and called it good.
In time, humanity harnessed the power of even more of the electromagnetic spectrum. And lo, the people of Earth told their truths, voiced their opinions, and advertised their wares and services in the digital realm.
And the people of Earth looked upon their works, and … well, that’s where all kinds of things got screwed up … particularly for news outlets.
Getting to the point
Of course, “screwed up” is a completely subjective interpretation of the current reality of the state of journalism. Still, I consider it appropriate. At least as it relates to digital marketing and social media. An advantage of my journalism career starting in 1997 and ending in 2018 is that I was able to watch in real time as journalism as a whole shifted to accommodate the new reality of the internet. I’ve also been able to watch as the rise and growth of social media was seemingly accompanied by a loss of many Americans’ critical thinking skills and, from there, a hyper-partisan nation where your political affiliation dictated your news source.
My biased version of history notwithstanding, there is no arguing that there has been a massive shift in how journalism is defined and perceived in this country. With the rise of the internet came the birth of social media. With social media came an expansion of where people could share their news and voice their opinions.
Where things got “screwed up,” as I said, is when people stopped looking at their opinions as their own thoughts and biases, and started perceiving them as “facts.” And then they spread these “alternative facts” (more on this later) via social media. And as the social media platforms gained power, and truth became more and more subjective, news organizations lost power.
Recent news
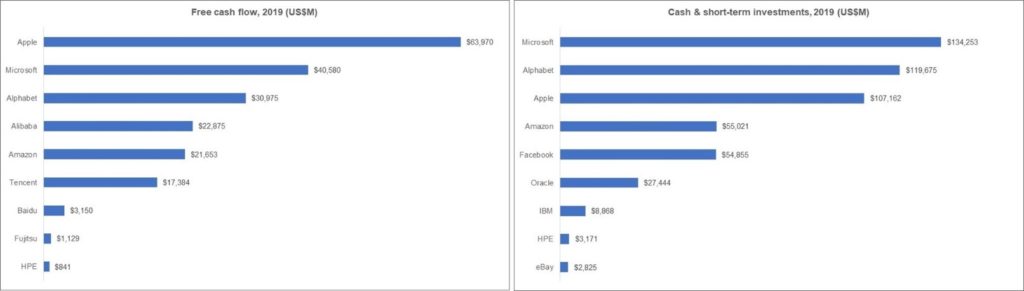
Digital advertising has fueled the growth of Facebook, Google, Baidu, Tencent, and other internet services companies. The companies don’t charge their users, which enhances the social media platforms’ popularity. Still, the proliferation of the social media platforms hasn’t been the best thing for the news business. Indeed, digital companies have been in the news fairly often in recent years, as has their connection to news outlets. A few examples:
- In fall 2019, it became apparent that the two reigning giants of digital advertising would have to acknowledge a third member of the club. Facebook and Google, which had ruled the industry for most of the decade, was about to be joined by Amazon. Indeed, Amazon’s advertising revenue has continued to grow, with even its 1Q20 numbers, from the beginning of the COVID-19 crisis, showing a year-over-year increase of 44 percent. Still, that growth comes with a price. Amazon is owned by Jeff Bezos, the owner of The Washington Post. The Post’s investigative reporting on President Donald J. Trump drew Trump’s wrath, and that rage spilled over onto Amazon.
- A growing number of companies, in response to the growing repercussions of the Black Lives Matter protests, have been removing their ads from Facebook. The companies have been declaring solidarity with the #StopHateForProfit boycott, which is being led by a coalition of civil rights groups. Among the more than 400 companies is the retailer Patagonia, which tweeted on June 21 that “Patagonia is proud to join the Stop Hate for Profit campaign. We will pull all ads on Facebook and Instagram, effective immediately, through at least the end of July, pending meaningful action from the social media giant.” In a later series of tweets, the company said:
“From secure elections to a global pandemic to racial justice, the stakes are too high to sit back and let the company continue to be complicit in spreading disinformation and fomenting fear and hatred. As companies across the country work hard to ensure that Americans have access to free and fair elections this fall, we can’t stand by and contribute resources to companies that contribute to the problem.”
- Amid this backdrop, media buying agency GroupM predicted that “digital advertising on platforms such as Google, Facebook and Alibaba is set this year to overtake spending on traditional media for the first time, a historic shift in market share that has been accelerated by the coronavirus pandemic. Excluding online ads sold by old media outlets such as news publishers or broadcasters, digital marketing is predicted to account for more than half the $530 (billion) global advertising industry in 2020, according to GroupM, the media buying agency owned by WPP.”
It is that latter point that shows the phenomenal power of digital advertising. Indeed, the Internet Advertising Bureau (IAB) has tracked U.S. digital advertising revenues almost since its beginning. To give you an idea of how much and how quickly digital advertising has grown, the IAB reported that, in 1996, revenues from such advertising had reached $267 million. By 2000, a mere four years later, that number had grown to $8.2 billion. as the calendar rolled forward, so, too, did the ad spending, soaring to $12.5 billion in 2005; $26.0 billion in 2010; $59.6 billion in 2015; exceeding $100 billion for the first time in 2018; and hitting $124.6 billion in 2019. That’s roughly 10 times the 2005 figure.
Is that spending worth it? According to Statista, the average return-on-investment for each dollar spent on digital advertising was about $11 in 2018, “making it the medium with the highest return on advertising spending (or ROAS).”
What does all this have to do with journalism?
A whole heck of a lot, actually.
A less biased history of technology and journalism
Journalism has always been fueled by three forces: retail sales, subscribers, and advertisers. When journalism was pretty much only newspapers and magazines, the businesses survived on revenue generated by the sales of copies in retail venues such as shops and newsstands; via paid subscriptions, which allowed the copies to be mailed to the recipients; and through what advertisers paid to have their wares and services mentioned in print.

In time, however, radio rose up. Although the first radio program was broadcast in Canada on December 24, 1906, it took several more years before the first radio news broadcast would occur. On Aug. 31, 1920, a Detroit radio station aired the first radio news broadcast. Shortly thereafter, for a one-time cost of purchasing a radio (as well as the cost of powering the device), listeners could hear news and entertainment without needing to pay for it. Unfortunately, sales of the radios themselves didn’t benefit the news outlets, and the subscription model didn’t work for radio, either. As a result, radio news outlets relied on corporate sponsorships and advertisers. Newspapers and magazines continued as normal, but kept a wary eye on their new competitor.
Television was next, with the 1922 transmission via radio waves of a still picture. The technology was improved in 1925, with the successful transmission of a live human face.
Meanwhile, the federal government decided to regulate these new technologies, starting with the Federal Communications Act in 1934. The law created the Federal Communications Commission (FCC). Here’s how the FCC was initially described, according to “That’s the Way It Is: A History of Television News in America,” by Charles L. Ponce de Leon:
(The FCC) was responsible for overseeing the broadcasting industry and the nation’s airwaves, which, at least in theory, belonged to the public. Rather than selling frequencies, which would have violated this principle, the FCC granted individual parties station licenses. These allowed licensees sole possession of a frequency to broadcast to listeners in their community or region. This system allocated a scarce resource—the nation’s limited number of frequencies—and made possession of a license a lucrative asset for businessmen eager to exploit broadcasting’s commercial potential. … As part of this process, they had to demonstrate to the FCC that at least some of the programs they aired were in the “public interest.” Inspired by a deep suspicion of commercialization, which had spread widely among the public during the early 1900s, the FCC’s public-interest requirement was conceived as a countervailing force that would prevent broadcasting from falling entirely under the sway of market forces.
In reality, however, the FCC tended to be “unusually sympathetic to the businessmen who owned individual stations and possessed broadcast licenses and made it quite easy for them to renew their licenses. They were allowed to air a bare minimum of public-affairs programming and fill their schedules with the entertainment programs that appealed to listeners and sponsors alike. By interpreting the public-interest requirement so broadly, the FCC encouraged the commercialization of broadcasting and unwittingly tilted the playing field against any programs—including news and public affairs—that could not compete with the entertainment shows that were coming to dominate the medium.”
The National Broadcast Company’s Red Network launched the first daily radio news program on Feb. 24, 1930. The Columbia Broadcasting System (CBS) followed on Sept. 29, 1930, with radio broadcaster Lowell Thomas as the host. Thomas made history again in 1939, when he simultaneously read a news report over radio and television, making it the first television news broadcast.

It wasn’t until Sept. 2, 1963, that the concept of a daily news program translated to television, when Walter Cronkite anchored the first daily half-hour news program on network television for CBS. For well over a decade, ABC, NBC, and CBS ruled television news – until the June 1, 1980, launch of the Cable News Network, better known as CNN. The creation of a 24-hour television news network forever changed the way news was delivered. In response, all three network broadcasters dropped their 30-minute daily programs and went on to create longer-form news shows, including morning news broadcasts.
Throughout all these changes, news outlets continued to operate pretty much as they had at the very beginning. Newspapers and magazines continued to rely on retail sales, subscribers, and advertising revenue. Radio and television broadcasters relied far more heavily on advertising revenue. As time marched on, both print and broadcast news outlets updated how they gathered and spread the news as technology evolved.
But their time-tested business models were about to be upended by one new technology that would change everything.
The advent of the Internet
The world-spanning phenomenon known as the internet began as a Department of Defense research project in 1969. A few quick facts about it, mostly courtesy of Vox:
- “The internet began as ARPANET, an academic research network that was funded by the military’s Advanced Research Projects Agency (ARPA, now DARPA).”
- “… In 1973, software engineers … began work on the next generation of networking standards for the ARPANET. These standards, known as TCP/IP, became the foundation of the modern internet. ARPANET switched to using TCP/IP on January 1, 1983.”
- “During the 1980s, funding for the internet shifted from the military to the National Science Foundation. The NSF funded the long-distance networks that served as the internet’s backbone from 1981 until 1994. In 1994, the Clinton Administration turned control over the internet backbone to the private sector. It has been privately operated and funded ever since.”
- As of April 2020, nearly 4.57 billion people “were active internet users,” encompassing 59 percent of the global population.
- And no, despite the hype, former Vice President Al Gore did not create the internet. In truth, he never claimed that he had. What he did say, in a 1999 interview with CNN, was he “took the initiative in creating the internet.” The actual inventors of the internet, TCP/IP designers Bob Kahn and Vint Cerf, have said that “Gore was “the first political leader to recognize the importance of the internet and to promote and support its development” — particularly with his sponsorship of the 1991 High Performance Computing and Communications Act (HPCCA). Kahn and Cerf say that law “became one of the major vehicles for the spread of the internet beyond the field of computer science.”
In 1994, three years after the HPCCA’s passage, the founding of Netscape and Yahoo! helped to kickstart mass-market adoption of the web and email, respectively. Online searches were simplified by Google’s arrival in 1998. Hundreds of other Internet companies were founded in the latter half of the 1990s — too many, as it turned out. However, the advertising-supported model of free Internet services survived the dotcom bubble’s collapse in 2001.

The trouble starts
In 2004, the Pew Research Center published its first annual State of the News Media Report. In the report’s inaugural edition, Pew noted that then-President George W. Bush had told ABC News in December 2002 that he “preferred to get his news not from journalists but from people he trusted, who ‘give me the actual news’ and ‘don’t editorialize.’” Indeed, a New Yorker writer noted that senior White House staff “saw the news media as just another special interest group whose agenda was making money, not serving the public – and surveys suggest increasingly that the public agrees.”
These observations were some of the earliest warnings that a sharply partisan divide was coming over previously agreed-upon norms such as truth, facts, and the mission of journalism. Indeed, the 2004 report went on to warn:
Some argue that as people move online, the notion of news consumers is giving way to something called “prosumers,” in which citizens simultaneously function as consumers, editors and producers of a new kind of news in which journalistic accounts are but one element.
With audiences now fragmented across hundreds of outlets with varying standards and agendas, others say the notions of a common public understanding, a common language and a common public square are disappearing.
For some, these are all healthy signals of the end of oligarchical control over news. For others, these are harbingers of chaos, of unchecked spin and innuendo replacing the role of journalists as gatekeepers over what is fact, what is false and what is propaganda. Whichever view one prefers, it seems everything is changing.
Sound familiar?
Going back to digital for a moment … among the 2004 Pew report’s conclusions, two items stand out:
- The biggest question may not be technological but economic…If online proves to be a less useful medium for subscription fees or advertising, will it provide as strong an economic foundation for newsgathering as television and newspapers have? If not, the move to the Web may lead to a general decline in the scope and quality of American journalism, not because the medium isn’t suited for news, but because it isn’t suited to the kind of profits that underwrite newsgathering.
- Those who would manipulate the press and public appear to be gaining leverage over the journalists who cover them. Several factors point in this direction. One is simple supply and demand. As more outlets compete for their information, it becomes a seller’s market for information. Another is workload. The content analysis of the 24 hour news outlets suggests that their stories contain fewer sources.
So, at the time, news outlets weren’t yet certain of what to make of using the internet to gather and disseminate news. And concerns about manipulation of the media were already on people’s radar.
The fuse is lit
The 2008 presidential campaign of Barack Obama, and his 2009 inauguration, exacerbated the racism and xenophobia of many White Americans. Fox News, which had been known for its motto of being “fair and balanced,” immediately launched racist attacks on Obama and his wife, Michelle:
- May 2008: Fox News contributor Liz Trotta joked that then-candidate Obama should be assassinated.
- June 6: On the Fox News program “America’s Pulse,” host E.D. Hill referred to a celebratory fist bump shared by the Obamas to celebrate his acceptance as the Democratic presidential nominee as a “terrorist fist jab.” Hill was dropped from her show a week later.
- June 11: A Fox News chyron referred to Michelle Obama as “Obama’s Baby Mama.”
Things would only deteriorate from there.
Amid the sharply partisan tone of Fox News and other conservative news outlets, the explosion in growth of social media platforms occurred. As the BBC noted:
Clearly the enabler of the modern form of “fake news” – or, if you like, misinformation – has been the explosive growth of social media.
“In the early days of Twitter, people would call it a ‘self-cleaning oven’, because yes there were falsehoods, but the community would quickly debunk them,” (says Clare Wardle of First Draft News, a truth-seeking non-profit based at Harvard’s Shorenstein Center). “But now we’re at a scale where if you add in automation and bots, that oven is overwhelmed.
“There are many more people now acting as fact-checking and trying to clean all the ovens, but it’s at a scale now that we just can’t keep up.”
One example of the latter comment is the proliferation of bots in social media. As has been noted elsewhere, bots serve a useful purpose for social media companies. Regrettably, they also represent a danger to social media platforms in that they can rapidly spread misinformation and propaganda. Indeed, the malicious use of bots helped sway public opinion in the 2016 election, in which Russia used them to help position Trump into a better position for him to win election to the presidency.
In addition, in 2009, an Ohio State University study warned that more Americans, rather than seeking to be informed by their news outlets, were instead increasingly flocking to news that reinforced their own prejudices. Conservatives headed to Fox News; liberals, to CNN and MSNBC.
Meanwhile, during Obama’s two terms in office, the Pew Research Center noticed something else happening to journalism: tech companies were increasingly becoming involved in their operations:
In 2013, the business of journalism saw another twist in its digital evolution: An influx of new money – and interest – from the tech world.
At this point, professional newsgathering is still largely supported by advertising directed to such legacy platforms as print and television and, secondarily, by audience revenues (mostly subscriptions). But other ways of paying for news are becoming more visible. Much of the momentum is around this high-profile interest from the tech world, in the form of venture capital and individual and corporate investments, which bring with them different skill sets and approaches to journalism.
But as the tech companies continued to invest, and more advertising shifted to the digital world, news outlets found themselves “competing for an increasingly smaller share of those dollars.” As a result, even as news outlets fought a battle against an increasingly partisan readership, it was also fighting a war on a different front: namely, against the impact and influence of technology companies and social media platforms. According to the conclusions in Pew’s 2016 report:
- It has been evident for several years that the financial realities of the web are not friendly to news entities, whether legacy or digital only. There is money being made on the web, just not by news organizations.
- Increasingly, the data suggest that the impact these technology companies are having on the business of journalism goes far beyond the financial side, to the very core elements of the news industry itself. In the predigital era, journalism organizations largely controlled the news products and services from beginning to end, including original reporting; writing and production; packaging and delivery; audience experience; and editorial selection. Over time, technology companies like Facebook and Apple have become an integral, if not dominant player in most of these arenas, supplanting the choices and aims of news outlets with their own choices and goals.
- The ties that now bind these tech companies to publishers began in many ways as lifelines for news organizations struggling to find their way in a new world. First tech companies created new pathways for distribution, in the form of search engines and email. The next industry overlap involved the financial model, with the creation of ad networks and app stores, followed by developments that impact audience engagement … Now, the recent accusations regarding Facebook editors’ possible involvement in “trending topics” selections have shined a spotlight on technology companies’ integral role in the editorial process.
Meanwhile, as the end of Obama’s second term neared, the lines of partisan perception had been drawn: CNN, MSNBC, The New York Times, The Washington Post, and many other news outlets were firmly perceived as “liberal.” Fox News, Breitbart, The New York Post and the Wall Street Journal were counted as “conservative.”

By June 16, 2015, when Trump descended an escalator in Trump Tower to announce his candidacy for the 2016 presidential election, the opposing forces of technology companies and news outlets were about to combust.
Things go boom
You know what happened next:
- The bot attacks from Russia that manipulated social media, influenced the very facts Americans used to vote, and continue to be a clear and present danger to American democracy.
- Fox News effectively becoming a part of the Trump campaign. Indeed, Fox News, Trump’s news outlet of choice during his campaign, stopped using its motto “fair and balanced” in August 2016 – one month after Trump was confirmed as the Republican presidential nominee. In June 2017, five months after Trump’s inauguration, Fox News officially dropped the motto.
Meanwhile, we’ve seen new phrases that shatter our understanding of once-simple concepts such as truth or facts. Trump advisor Kellyanne Conway coined the phrase “alternative facts” on Jan. 21, 2017, in an effort to defend false estimates by then White House press secretary Sean Spicer on the size of the crowd gathered in Washington for Trump’s inauguration.
And, of course, there is “fake news,” which was popularized by Hillary Rodham Clinton in a speech on Dec. 8, 2016. While refuting the Pizzagate conspiracy theory, she noted “the epidemic of malicious fake news and false propaganda that flooded social media over the past year. It’s now clear that so-called fake news can have real-world consequences. This isn’t about politics or partisanship. Lives are at risk… lives of ordinary people just trying to go about their days, to do their jobs, contribute to their communities.”
Less than a month later, then-President-elect Trump made use of the phrase during press conference in which he said “you’re fake news” to CNN reporter Jim Acosta. A day or so later, on Jan. 11, 2017, he tweeted (in all-caps) about various news investigations into his political and business dealings, “FAKE NEWS – A TOTAL POLITICAL WITCH HUNT!” Since then, he’s made “fake news” a standard response to virtually any news report that casts him in a negative light.
And that brings us to today, when Americans are increasingly growing wary of the role social media platforms play in delivering the news… particularly when those platforms have been shown to be receptive to inflammatory points of views. The current ad boycott of Facebook is but one example.
The reach of technology companies, political partisanship, and social media platforms has had a definite impact on modern journalism. Unlike previous technological advances such as radio and television, digital technology’s influence on news outlets has changed the very nature of journalism, as well as how journalism is perceived. Indeed, even as more than half of Americans get their news from social media, a Pew Research Center study shows that:
- Almost all Americans – about nine-in-ten (88%) – recognize that social media companies have at least some control over the mix of news people see.
- About six-in-ten (62%) say social media companies have too much control over the mix of news that people see on their sites, roughly four times as many as say that they don’t have enough control (15%).
- Just 21% say that social media companies have the right amount of control over the news people see.
- While social media companies say these efforts are meant to make the news experience on their sites better for everyone, most Americans think they just make things worse. A majority (55%) say that the role social media companies play in delivering the news on their sites results in a worse mix of news.
- About eight-in-ten U.S. adults (82%) say social media sites treat some news organizations differently than others
- As large majorities say that the tone of American political debate has become more negative in recent years, about a third of U.S. adults (35%) say that uncivil discussions about the news are a very big problem when it comes to news on social media. Additionally, about a quarter (27%) say that the harassment of journalists is a very big problem associated with news on social media.
The questions that remain are simple:
- Will we continue to tolerate the outsized influence of technology companies on journalism?
- Should social media companies be legally required to police the accuracy of their content?
- Should social media platforms ban all political advertising?
- Will Americans see the value of paying a fee for news content, as long as the content is objective and of high quality?
- And, finally, will Americans see past their own prejudices to force news outlets to present news that is not only factually accurate, but free from bias?
Time will tell.
About the author
Melvin Bankhead III is the founder of MB Ink Media Relations, a boutique public relations firm based in Buffalo, New York. An experienced journalist, he is a former syndicated columnist for Cox Media Group, and a former editor at The Buffalo News.
Note from MTN Consulting
MTN Consulting is an industry analysis and research firm, not a company that typically comments on politics. We remain focused on companies who build and operate networks, and the vendors who supply them. That isn’t changing. However, we are going to dig into some of the technology issues related to these networks and networking platforms which are having (or will have) negative societal effects.
–
Image credits: (1) iStock, by Getty Images (cover); (2) Will Francis; (3) CBS; (4) Shutterstock; (5) CNN‘s Twitter feed.